S7 PLC Block Decompiler
The S7 PLC block decompiler extension provides support for reverse engineers and security auditors to analyze Siemens Simatic S7 PLC programs.
Overview.
The S7 PLC block decompiler is a response to the rise in complexity of PLC programs and the growing needs to assess code running on PLC for security and safety purposes.
This JEB extension provides the following features:
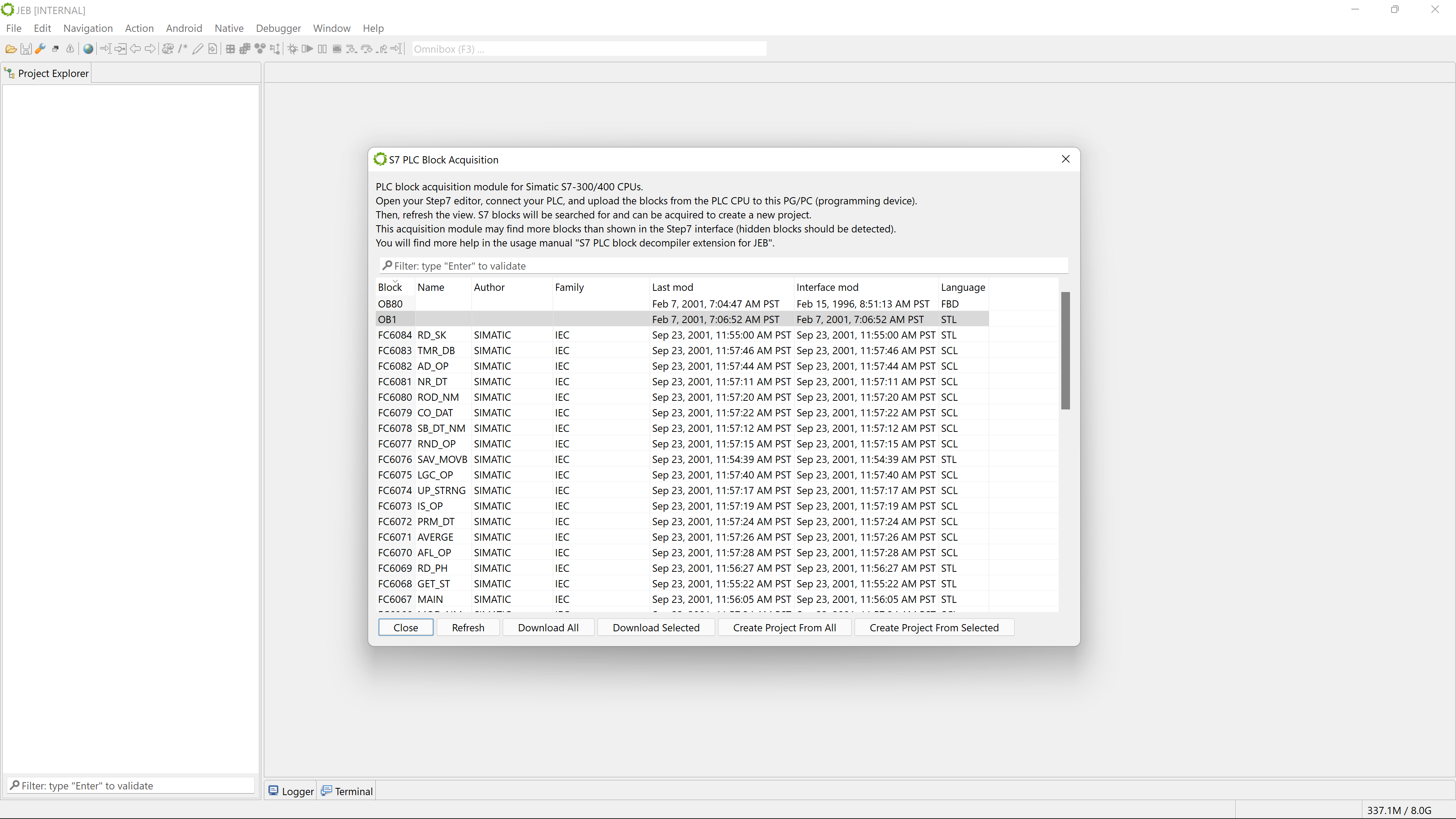
- Acquire S7 opaque binary blocks for S7-300 and S7-400 CPUs.
- Parse and explore S7 blocks.
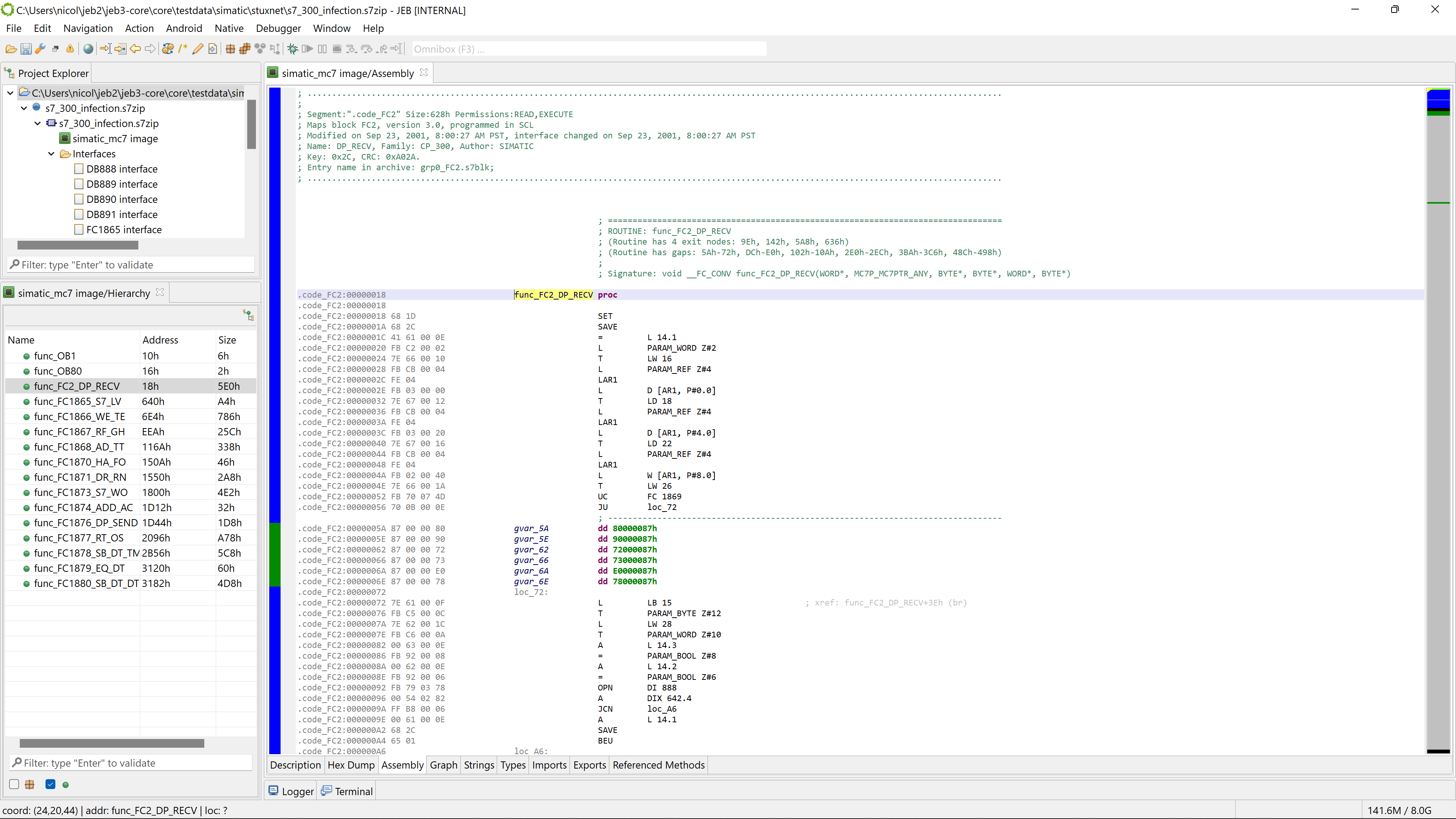
- Disassemble MC7 programs.
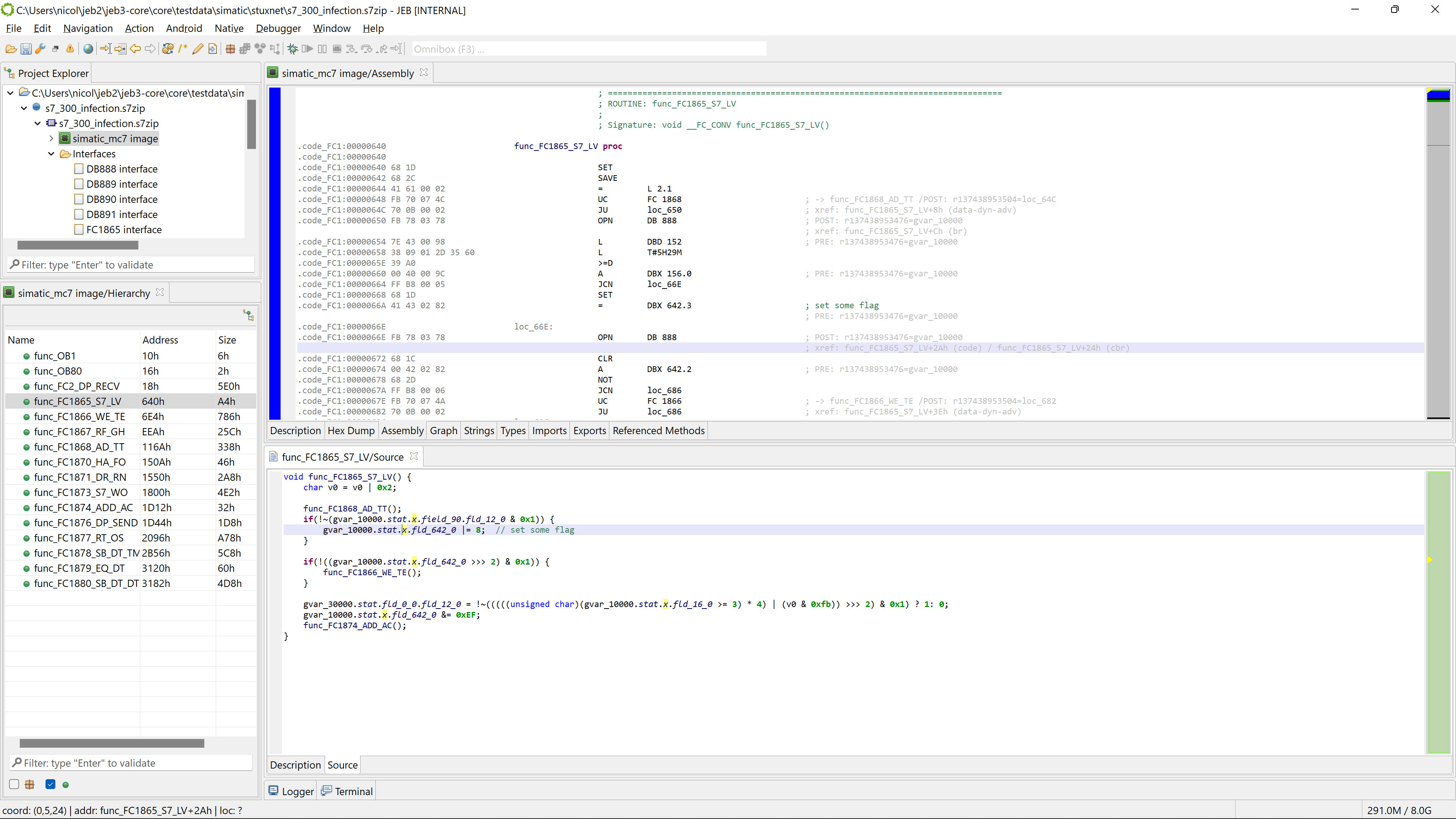
- Decompile to pseudo-C source code (*).
- Use the JEB API to write extension plugins to further analyze the code.
Learn about reversing S7 blocks on our blog.
(*) The S7 decompiler has limitations. Some are inherent to decompilation itself, some will be lifted as the extension matures and missing features are added. Currently, the decompiler cannot process all types of MC7 code: Treatment of timers and counters is limited, nested STL operations ('A(', 'O(', ')', etc.) or MCR-dependant code is not supported, multi-instance blocks are not supported as well.
Details.
Analyze S7 blocks, disassemble and decompile MC7 code.
Siemens Simatic PLC can be programmed using a variety of languages, including ladder logic, low-level STL (Statement List, assembly-like) and higher-level SCL (Structured Control Language, Pascal-like). Regardless of the source type, the program is compiled to MC7 bytecode, a machine code representation of the networks, and packed into opaque binary blobs that contain interface definitions, metadata elements, and code. Blocks are downloaded onto S7 PLC, such as S7-300/S7-400 or newest S7-1200/S7-1500 (not supported by this JEB extension).
The S7 PLC block decompiler can parse such blocks.
- Metadata (e.g. timestamps, authoring information, etc.) is extracted.
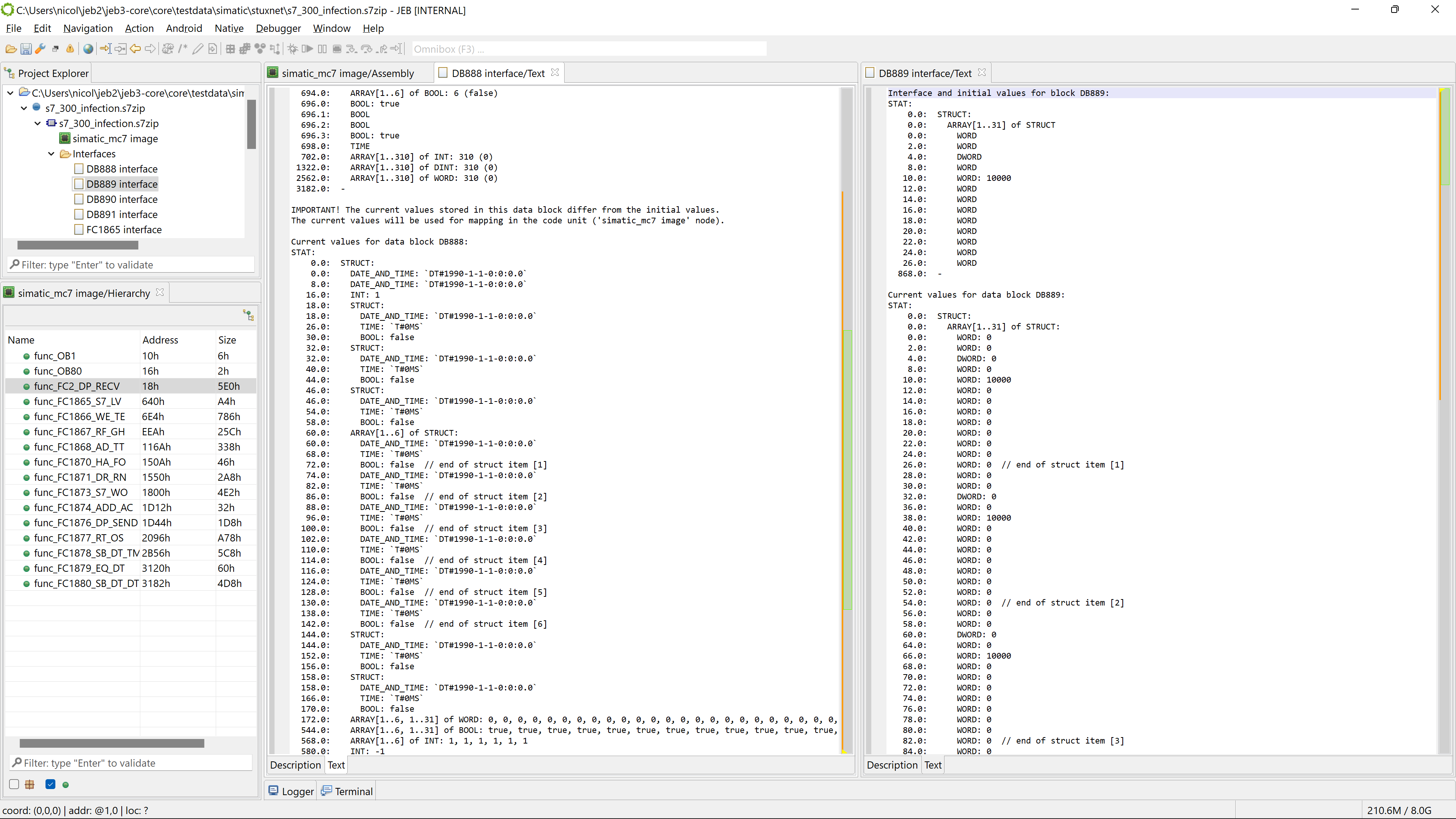
- Block data structures (interfaces) are parsed.
- MC7 opaque bytecode is disassembled to STL and decompiled to pseudo C code.
Decompilation is crucial when it comes to analyzing unknown and/or large PLC code, for example for black-box auditing or security research purposes. It is easier for a reverse engineer to navigate and massage C code than pouring through thousands of obscure lines of MC7 or STL code.
Annotate and refactor your analysis.
To make the analysis of unknown or obfuscated code as easy as possible, JEB provides a flexible output.
Among other things, JEB allows the user to:
- Comment the assembly code and high-level decompiled code.
- Rename variables, routines, functions, etc.
- Navigate cross-references of code and data.
Leverage the JEB API to automate reverse engineering tasks.
Using Java or Python, users can write their own scripts and plugins to automate some tasks of reverse engineering process. For example, the analyst may want to look for specific code patterns, or they may want to find and highlight relationships between areas of code automatically.
The API also allows power users to perform advanced static analysis on the code, for example to track register and data usage, which can be used to determine unwanted code conditions or potential bugs.
Licensing.
The S7 PLC block decompiler extension is availble with JEB Pro and JEB Pro Floating licenses.
Team.
The S7 PLC block decompiler is developed by Nicolas Falliere and his team.
In 2010/2011, while doing security research and malware analysis for Symantec Corporation, Nicolas spent countless hours on the Stuxnet malware. He reverse-engineered the malicious code that infected S7-300 and S7-400 PLC to thwart uranium enrichment centrifuges, and was the first to publish a detailed description of the attack sequence.