JEB Decompiler for MIPS


Our MIPS processor and microcontroller machine code decompiler allows reverse engineers and security auditors to analyze malicious MIPS programs and audit complex embedded systems.
Features
Coupled with the power of JEB, our MIPS 32-bit decompiler provides the following unmatched features:
- Augmented disassembly including resolution of dynamic callsites and syscalls, candidate values determination for registers, dynamic cross-references, etc.
- Decompilation to pseudo-C source code.
- Advanced optimization passes to thwart protected or obfuscated code.
- Interactive layer allowing refactoring: type definition, stackframe building, renaming/commenting/cross-referencing, etc.
- Full API to perform advanced and/or automated code analysis in Python or Java.
Demo
The video below shows our MIPS decompiler in action against the infamous Mirai IOT malware.
You may also download and try out the latest JEB MIPS Decompiler demo.
Technical Details
MIPS programs exhibit a level of complexity that even experienced reverse-engineers may feel overwhelmed or unprepared to deal with.
Unlike well understood and well practiced Intel x86 machine code, even the simplest of operations do not seem to "stand out" in a MIPS disassembly.
Not to mention other intricacies inherent to a RISC instruction set, such as unaligned reads and writes; or counter-intuitive idioms closely tight
to the MIPS architecture itself, such as the branch delay slots or seemingly opaque code blocks.
A strong decompiler is a precious tool to deep dive into MIPS code efficiently.
A strong decompiler is a precious tool to deep dive into MIPS code efficiently.
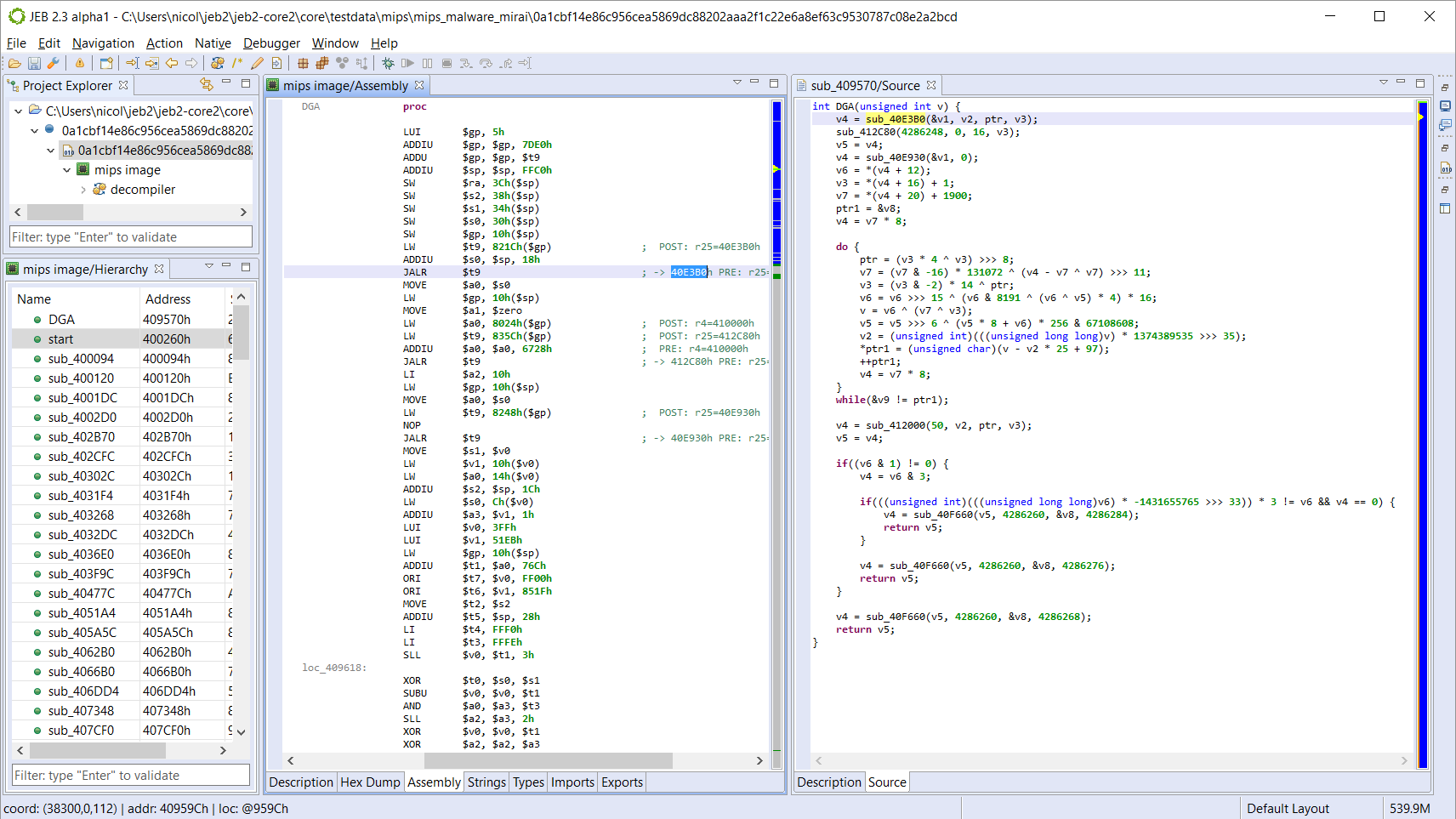
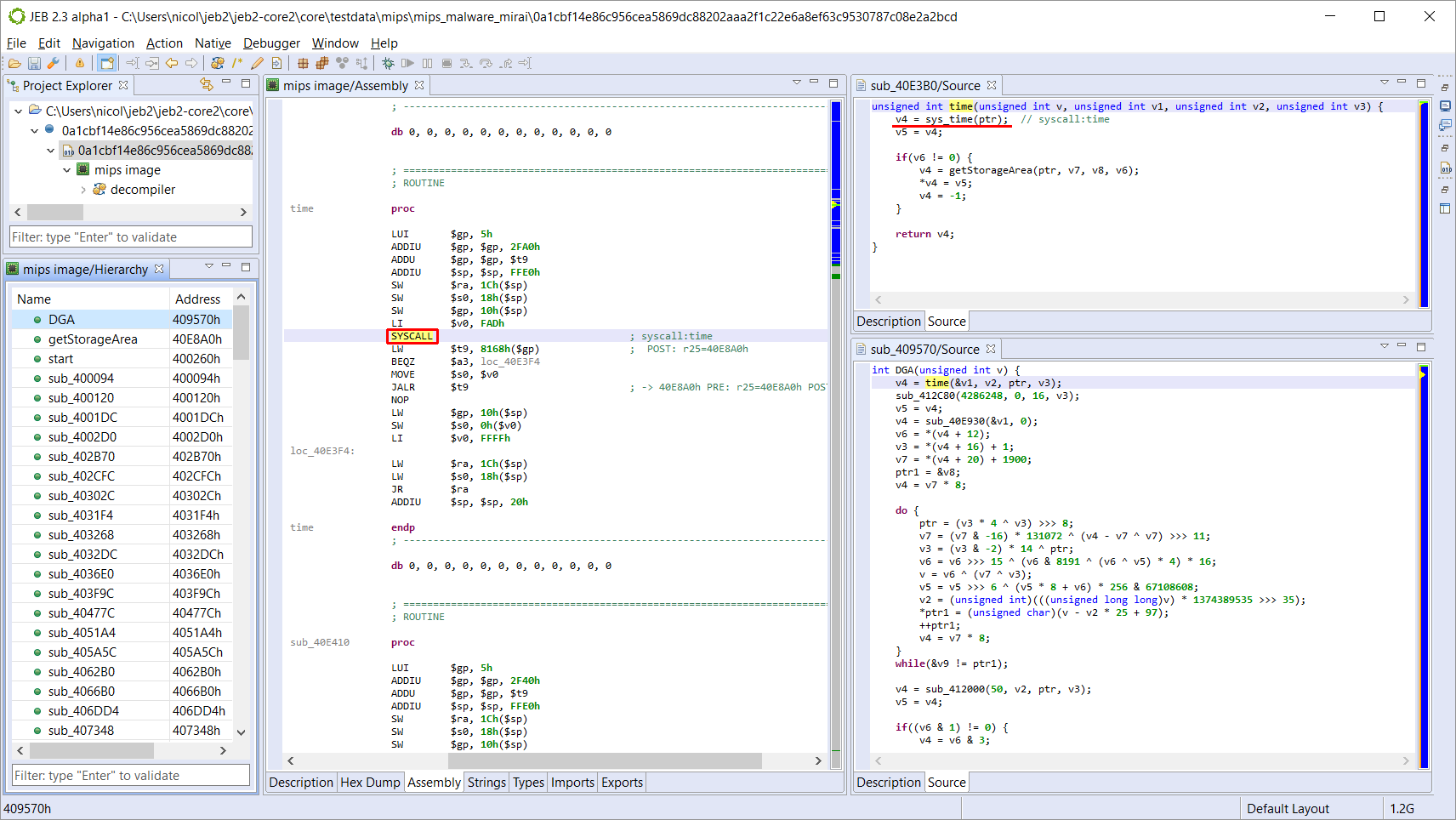
As is the case with any RISC machine, MIPS code can be fairly complicated to read. Having a strong decompiler providing pseudo-code is an incredible time saver to reverse-engineer malicious or clean code alike. The picture above shows side-by-side disassembly and decompiled C code of the Domain Generator Algorithm routine of a closed-source strain of Mirai found in the wild. The output is fully interactive, and support everything an analyst may expect: cross-references, commenting, renaming, typing (stackframe definition, globals, custom types), even refactoring via the creation of packages.
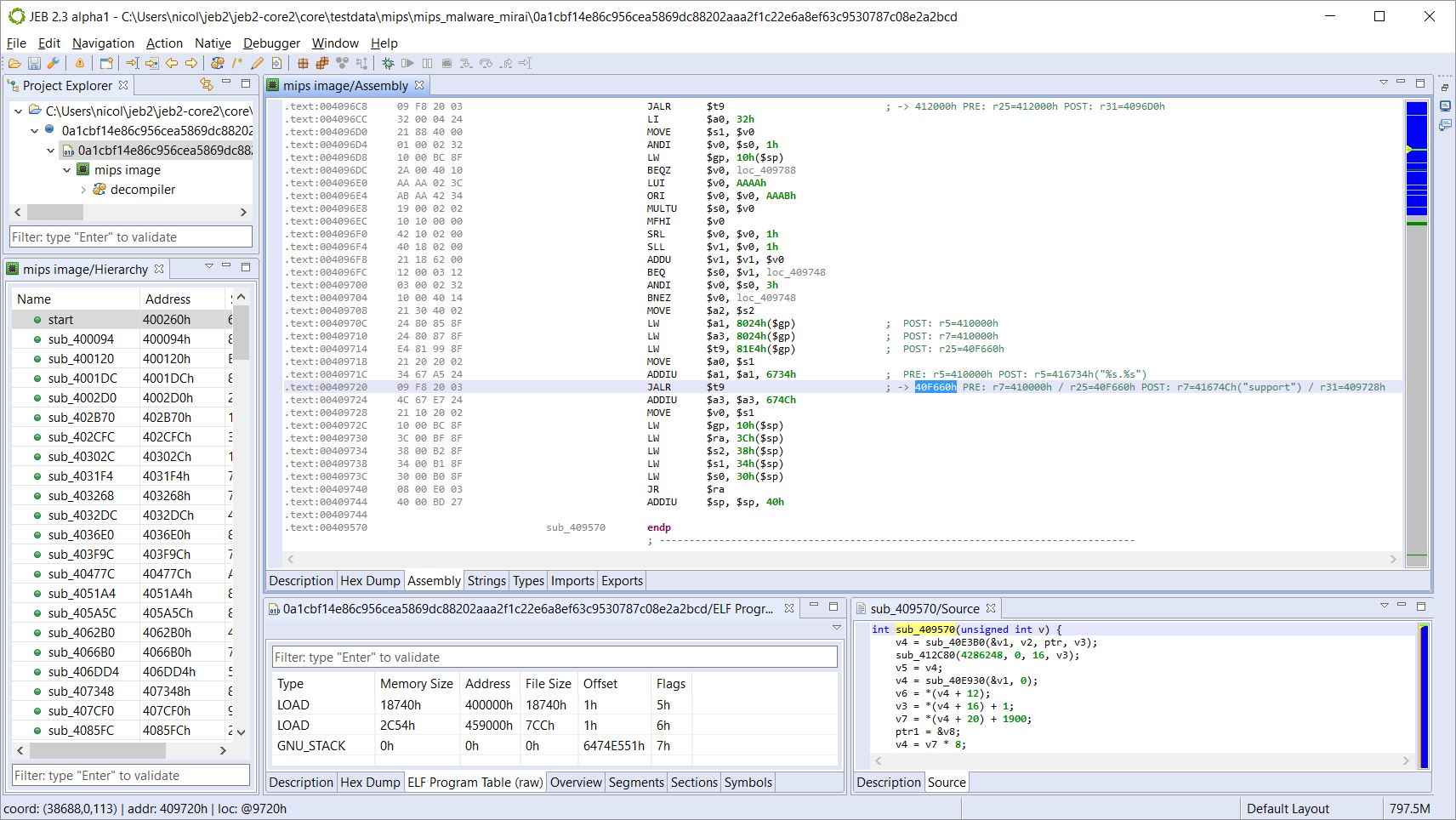
The picture above shows the augmented assembly view with dynamic references resolved. (Note the references to a string "support" in register $a3 after execution of the delay slot; note the target branch address held in $t9.) Optimized MIPS code commonly references data items and code routines dynamically. Augmenting the assembly view to provide information such as jump and branch targets as well as register values ahead of time is crucial to allow fast navigation of the disassembly.