Let’s have a quick look at a variant of Android.Uracto, an app that steals (and potentially spams) contacts from Android devices. There is nothing particularly interesting about this piece of malware, but it’s the occasion to demonstrate some of JEB less-known and forthcoming abilities.
Upon startup, the app displays the following spinner, that translates to “Reading the articles…”:
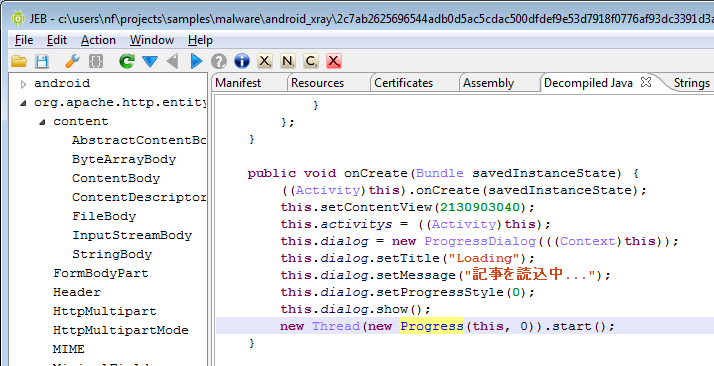
The onCreate() method for the main activity displays the above spinner, and also starts a new Thread, that will create and run a Progress object. Here it is:
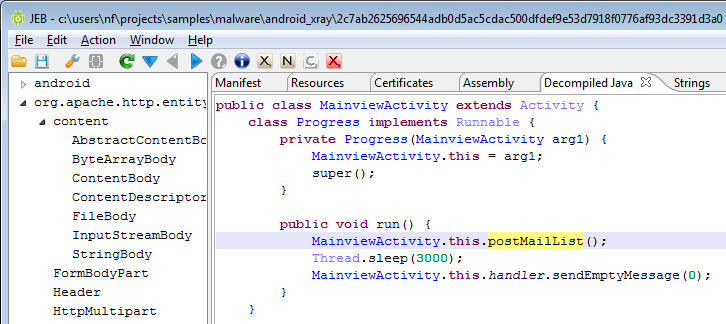
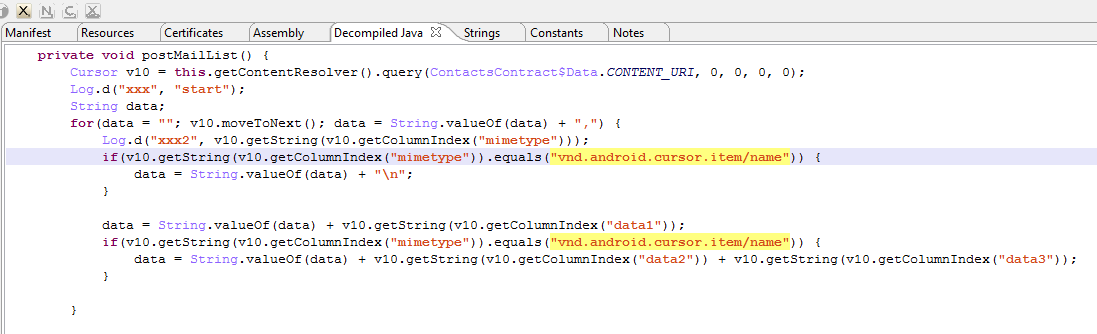
The run() method will call postMailList(). This method gets the ContentResolver for the app, and enumerates all entries having the “vnd.android.cursor.item/name” MIME type. According to the documentation, these entries represent “contacts’ proper names”.
A buffer representing the data1, data2, and data3 fields (respectively, Display Name, Given Name, and Family Name) is dynamically created.
[JEB specific]
Notice the optimizations that allowed the creation of that compact construct:
- for-loop optimization
- string concatenation
- aggressive variable substitution
Some of these optimizations are already present in 1.0.x, others will be included in the 1.1 versions.
[/JEB specific]
The final data (“contact1, contact2, …”) is dumped on the external memory storage, encoded and POST’ed to hxxp://jap2012.com/data/main.php.
Find the decompiled activity here: solution.newsandroid.MainviewActivity
Sample MD5: ba73e96caa95999321c1cdd766bdf58b