JEB 2.3.11 is out – We’re getting close to completion on our 2.3 branch! 1
Before we get into the matter of this blog post, a couple of noteworthy changes in terms of licensing:
- The Android Basic builds require an active Internet connection; however, if the JEB license is current, we allow a much longer grace period before requesting a connection with our licensing server. This is to take care of scenarios where the connectivity would drop for a relatively extended period of time on either end.
- Most interestingly, expired licenses of all types may now be used past their expiration date to reload and work on existing JDB2. New projects cannot be created with expired licenses though.
In terms of features, JEB 2.3.11 includes upgrades to our ARM64, MIPS64 and x86-64 parsers 2, as well as fixes and additions to the DEX parser. One interesting update, which prompted writing this blog post, is the support of DEX 39 opcodes.
DEX 39 Opcodes
Here they are, per the official documentation:
- const-method-handle vAA, method_handle@BBBB
- const-method-type vAA, proto@BBBB
Version 39 of the DEX format will be supported with the release of Android P 3. DEX 38 had been introduced to support Oreo’s new opcodes related to dynamic programming. We wrote a lengthy post about them on this very blog.
The new instructions const-method-handle and const-method-types are natural additions to retrieve method handles (basically, the same as a function pointer in C, a concept foreign to the JVM until lambdas and functional-style programming made its way into the language) and method prototypes. Those opcodes simply query into the prototypes and handles pools.
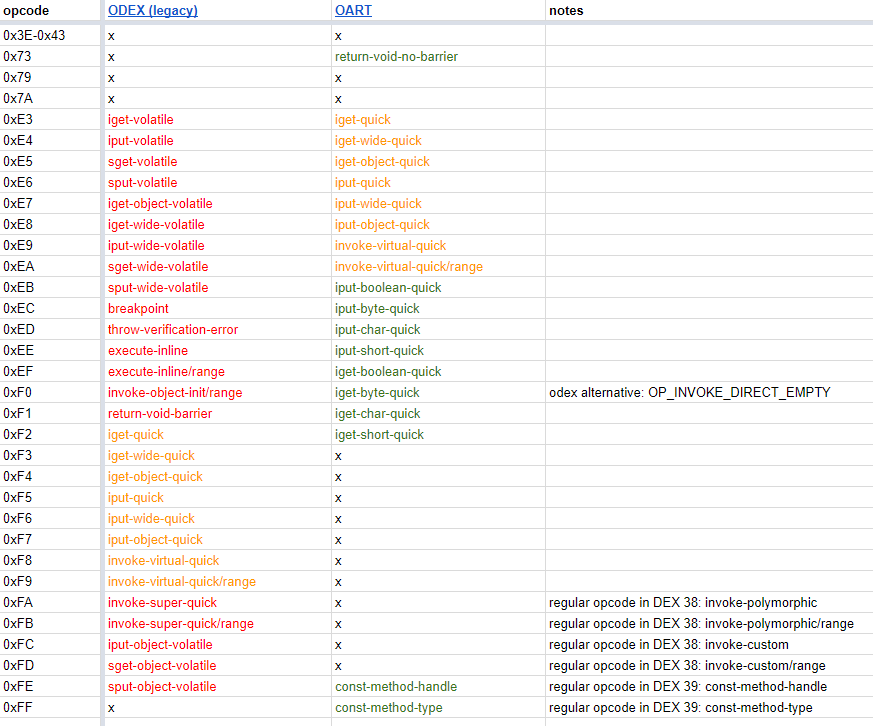
In fact, support for those two opcodes was added in JEB months ago, right after their introduction in ART, which dates back to September 2017 (AOSP commit). Now, if you’ve been following through the Dalvik, DEX and ART intricacies, you may know that we are facing opcode overlaps:
- The original non-optimized DEX instruction set spans from 0 to 0xFF, with undefined ranges (inclusive brackets omitted for clarity): 3E-43, 73, 79-7A, E3-FF
- DEX 38 defines the range FA-FD (4x new invoke-xxx)
- DEX 39 defines the range FE-FE for the aforementioned new opcodes (2x new const-method-xxx)
- The now defunct optimized DEX (ODEX) set, predating ART, used the reserved sub-range E3-FE
- The deadborn extended set used FF as an extension code to address 2-byte opcodes (FFxx); they were defined but unimplemented in Ice Cream Sandwich, and removed soon after in Jelly Bean.
- Finally, ART opcodes: also used for optimizing DEX execution, those opcodes use the 73 and E3-FF ranges
ART opcodes in E3-FE are not necessarily the same as the original ODEX’s! The following table recaps the differences between ODEX and OART:
When you feed a piece of optimized DEX file to JEB, it may not know which instruction set to use. Normally, the following rules apply:
- For stand-alone (within or outside an APK) DEX files advertising a version code less than or equal to 37, the legacy ODEX set would be used if any opcodes within that range are encountered;
- For DEX files with version 38 or above, or that are part of an OAT ELF file, the newer ART set will be used.
However, if the determination is incorrect (eg, you are opening a stand-alone DEX 37 file using ART opcodes), you may manually specify which optimized opcodes set the Dalvik parser should use by opening the project’s settings (Edit/Options, Advanced…), and setting the property DalvikParserMode 4 to:
- 0: legacy DEX (default value)
- 50: ART
- 100: DEX 38
- 110: DEX 39
- 1000: latest
That’s it for today’s DEX clarifications. Remember to upgrade to JEB 2.3.11. On a side-note, let us know if you’d like to be part of our group of early testers: those users receive beta builds ahead of time (eg, JEB 2.3.12-beta this week).
Thank you.
—
- A couple more updates are in the pipe before we start publishing betas of JEB 3. ↩
- The x86 modules now support the newest AVX-512 instruction set, although we do not decompile it ↩
- Per Google’s habits, we may expect a beta of Android P with API level 28 this Spring ↩
- That property is not as accessible as we’d like; an upcoming update will clarify and improve the UX around that. ↩