Updated on May 4: JEB 2.2.3 is out. All users can now use the Android debugger modules.
In this short post, we will show how the debuggers API can be used to monitor an app execution, hook into various key methods and classes of the standard Java cryptography SPI, and extract input and output data, as they flow in and out encryption/decryption routines.
Very handy to retrieve encrypted data used within an app or exchanged with a remote server. 1 Check out the following video to see what we are talking about:
The sample code of the AndroidCryptoHook plugin can be found on our public GitHub repository.
This simple plugin does the following:
- It looks for an active Dalvik debugging session
- It sets up a debugger listener, which will listen for BREAKPOINT and BREAKPOINT_FUNCTION_EXIT events
- It currently “hooks” 3 methods of the javax.crypto.Cipher abstract class:
- byte[] doFinal(byte[] input)
- int doFinal (byte[] output, int outputOffset)
- int update(byte[] input, int inputOffset, int inputLen, byte[] output)
- When any of the hooked method is called, the associated hook onEntry method is executed, which will dump interesting input parameters
- When the same hooked method returns, the associated hook onExit method is executed, which will dump interesting exit parameters and return value
The hook here consists of a double breakpoint, one triggered when a method is entered, another one, when it exits.
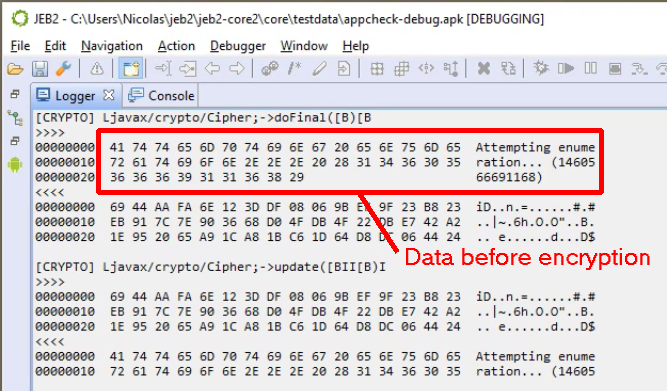
The code for that Java plugin is fairly simple. More hooks could be easily added, and hooks in native libraries could be set up in a similar fashion. Lastly, always keep in mind that the API in general (and this plugin in particular) can be leveraged by UI or headless clients. Automate things away if you need to.
The one and only entry-point for developer resources is our Developer Portal. Do not hesitate to reach out, publicly or privately, if you have issues or pointed questions. Thank you.
- Dynamic execution monitoring can be achieved in several ways. Debugging a target is one of them. ↩
This blog post made my birthday 🙂
does this work with reflections?
That’s a great question that we forgot to mention – yes, it does: Reflection or not, the Cipher methods are at the end of the road.