This is the first post of a 3-part blogs series that will demonstrate the new features of JEB’s jeb.api.ast API package.
Classes of this package allow read and write access on the Abstract Syntax Trees (AST) of the decompiled Java code produced by JEB. In a nutshell, it allows power users to implement complex deobfuscation schemes or their own optimizations strategies.
Download the script
Demo video
Let’s jump straight to the crux of the matter: this piece of code has been obfuscating by a well-known Android/Java protector software:
/*.method public constructor (Context, AttributeSet, I)V .registers 8 const/4 v3, 0x1 const/4 v2, 0x0 invoke-direct View->(Context, AttributeSet, I)V, p0, p1, p2, p3 new-instance v0, Paint :E packed-switch v3, :90 :14 packed-switch v2, :A0 :1A goto :14 :1C invoke-direct Paint->()V, v0 iput-object v0, p0, TileView->b0431бб0431б0431:Paint :26 packed-switch v2, :B0 :2C packed-switch v2, :C0 :32 goto :2C :34 sget-object v0, xxxkkk$xkkxkk->b04310431б0431б0431:[I invoke-virtual Context->obtainStyledAttributes(AttributeSet, [I)TypedArray, p1, p2, v0 move-result-object v0 const/16 v1, 0xC invoke-virtual TypedArray->getInt(I, I)I, v0, v2, v1 move-result v1 :4C packed-switch v2, : D0 :52 packed-switch v2, :E0 :58 goto :52 :5A packed-switch v2, :F0 :60 packed-switch v3, :FC :66 packed-switch v3, :10C :6C goto :66 :6E packed-switch v2, :11C :74 packed-switch v3, :12C :7A goto :74 :7C packed-switch v2, :13C :82 sput v1, TileView->bб0431ббб0431:I invoke-virtual TypedArray->recycle()V, v0 return-void .packed-switch 0x0 :E :1C .end packed-switch .packed-switch 0x0 :1C :E .end packed-switch .packed-switch 0x0 :34 :26 .end packed-switch .packed-switch 0x0 :34 :26 .end packed-switch .packed-switch 0x0 :5A :4C .end packed-switch .packed-switch 0x0 :5A :4C .end packed-switch .packed-switch 0x0 :60 .end packed-switch .packed-switch 0x0 :4C :6E .end packed-switch .packed-switch 0x0 :4C :6E .end packed-switch .packed-switch 0x0 :7C :4C .end packed-switch .packed-switch 0x0 :4C :7C .end packed-switch .packed-switch 0x0 :82 .end packed-switch .end method*/JEB decompiles this Dalvik bytecode to the following Java code:
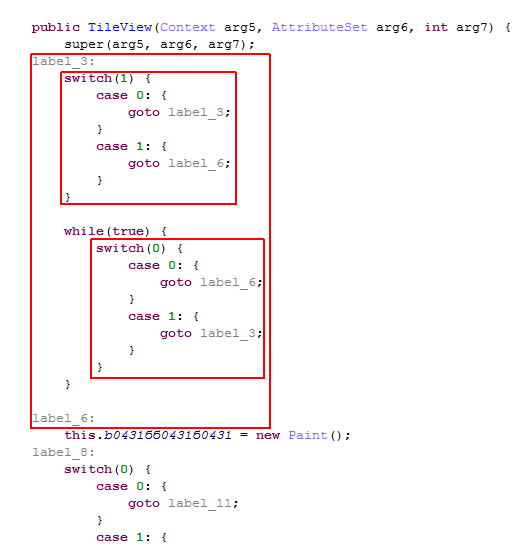
public TileView(Context arg5, AttributeSet arg6, int arg7) { super(arg5, arg6, arg7); label_3: switch(1) { case 0: { goto label_3; } case 1: { goto label_6; } } while(true) { switch(0) { case 0: { goto label_6; } case 1: { goto label_3; } } } label_6: this.b0431бб0431б0431 = new Paint(); label_8: switch(0) { case 0: { goto label_11; } case 1: { goto label_8; } } while(true) { switch(0) { case 0: { goto label_11; } case 1: { goto label_8; } } } label_11: TypedArray v0 = arg5.obtainStyledAttributes(arg6, xkkxkk.b04310431б0431б0431); int v1 = v0.getInt(0, 12); label_15: switch(0) { case 0: { goto label_18; } case 1: { goto label_15; } } while(true) { switch(0) { case 0: { goto label_18; } case 1: { goto label_15; } } } label_18: switch(1) { case 0: { goto label_15; } case 1: { goto label_21; } } while(true) { switch(1) { case 0: { goto label_15; } case 1: { goto label_21; } } } label_21: switch(0) { case 0: { goto label_24; } case 1: { goto label_15; } } while(true) { switch(1) { case 0: { goto label_15; } case 1: { goto label_24; } } } label_24: TileView.bб0431ббб0431 = v1; v0.recycle(); }As one can see, dummy switches as well as pseudo-infinite loops have been inserted within the original Java code, in order to produce flow obfuscation. Using the AST API, we’re going to implement a JEB plugin that cleans the obfuscated code.
A dummy switch construct looks like the following:
switch(X) { case X: goto next; case Y: goto label_fake1: case Z: goto label_fake2: } ... next:The above piece of code is equivalent to:
goto next; ... next:Which can be reduced to a single label:
next:In order to find the dummy switches, the JEB script is going to do the following:
- Recursively enumerate the statements of a method body, looking for SwitchStm elements
- Check that the switch is a dummy switch:
- The switched expression must be a Constant
- The case block associated with that constant must start with a Goto statement
- Replace the switch by the goto
- Find the first Label that follows the (now replaced) switch
- If a label is found, is at the same block level as the switch, and is the label pointed to by the goto that replaced the switch, then all the expressions between the goto and the label can be discarded
- Finally, apply standard JEB optimizations that remove the remaining useless gotos and labels
This algorithm fits in a less than a 100-line Python script. Download the script, experiment with it, and get accustomed to the API.
The cleaned-up code is this very simple, more readable method:
public TileView(Context arg5, AttributeSet arg6, int arg7) { super(arg5, arg6, arg7); this.b0431бб0431б0431 = new Paint(); TypedArray v0 = arg5.obtainStyledAttributes(arg6, xkkxkk.b04310431б0431б0431); int v1 = v0.getInt(0, 12); TileView.bб0431ббб0431 = v1; v0.recycle(); }In Part Deux, we will show how the AST API can be leveraged to decrypt encrypted strings of a protected piece of code.
Error executing python script:
java.lang.RuntimeException
I read your official blog, and found that your ASTRemoveDummySwitch code is too old, and the library files contained in it are not found, so it cannot be applied to the new version. I suggest you update it, and could you please send me the latest code about this script? Thank you very much!