Note: Download a demo of JEB Decompiler here.
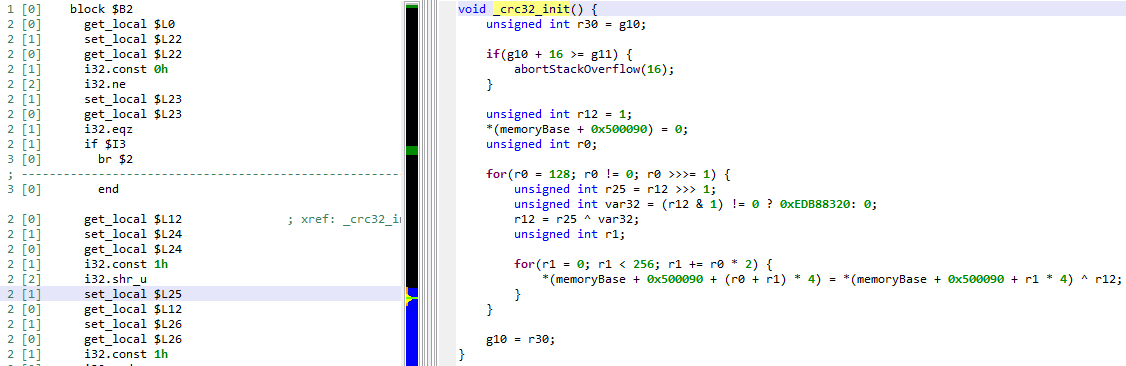
We published a paper deep-diving into WebAssembly from a reverse engineer point of view (wasm format, bytecode, execution environment, implementation details, etc.).
The paper annex details how JEB can be used to analyze and decompiler WebAssembly modules.
Thank you – Nicolas.

i want to try it ,thank u 🙂
hello 🙂 Our demos are available here: https://www.pnfsoftware.com/jeb/demo
thank you – nicolas