Update (11/2): parts 7 and 8 are available.
Our tutorials are available on the JEB2 developer portal, which aggregates all resources for API developers:
JEB2 Developer Portal
Update (11/2): parts 7 and 8 are available.
Our tutorials are available on the JEB2 developer portal, which aggregates all resources for API developers:
This blog assumes that JEB version 2.1.0 or above is used along with the OAT plugin 1.0.2 or above.
Parsing support for optimized DEX files was added to JEB2 to allow the analysis of non-deodex’ed files. Since ODEX files are target-dependant, the executing Dalvik VM is no longer restricted to regular opcodes. ODEX files may make use of “illegal” opcodes, optimized opcodes, or even the once regular but now dead extended opcodes. Whenever possible, parsing will take place, and instructions displayed in the assembly view.
In the screenshot below, note that opcode 43h (illegal for non-optimized code) is used, as well as iput-wide-volatile (optimized opcode for field access).
In that second screenshot, notice the use of a non-standard jumbo opcode.
If you are analyzing an extracted ODEX file (one whose header bytes start with “dey\n”), then all versions of JEB2 shall be able to process it. The Project tree will look like the following (project > artifact > odex unit > dex unit):
If you are analyzing an OAT file (DEX file precompiled to native and ready to run within the ART runtime), then you will need one additional plugin: the OAT plugin. This plugin can be registered on Business and Enterprise versions of JEB2. (Note: older versions of JEB 2.0, mainly versions 2.0.12 and above, require the third-party ELF plugin as well.)
Installation steps:
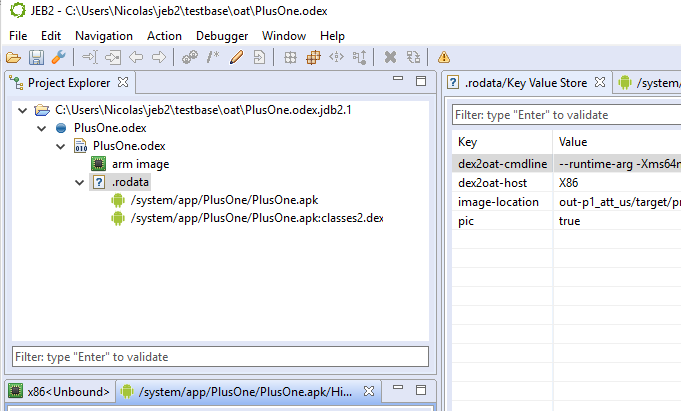
Now, you may open an OAT file. The project view should be similar to the following (project > artifact > elf unit > oat unit > dex or odex unit):
Here is another example of an ELF file containing an OAT section, containing 2 optimized DEX files:
That is it for this blog post. We are planning to release more documentation and tutorials about our APIs In the coming days. In the meantime, remember to check our open-source plugins on GitHub, they are great starting points for anyone interested in writing their own parsers or back-end plugins. Stay tuned, and happy analysis.
With the constant improvement of our UI client, new plugins, the upcoming release of the Dalvik debugger, as well as the APIs, JEB2 has become increasingly complex and full-featured.
In order to reduce the barrier of entry for new users, we are going to publish a series of introductory videos aiming to explain how to get started with JEB2 and how to use the RCP client to the fullest. We will strive to keep the videos short and concise, highlighting specific features and gotchas of our software.
You will find the YouTube “JEB2 Discovery” playlist here:
Dear users,
We are glad to announce that JEB2 is now available to all our customers!
If you have a valid JEB 1.x license, you should have received an equivalent build with a subscription valid till the end of your support period. If this is not the case, please reach out to support@pnfsoftware.com.
Additional documentation and resources can be found on our website. We are also providing PDF analysis support to all business/enterprise customers! The JEB2 PDF plugin can be downloaded here: https://www.pnfsoftware.com/
Open-source plugins and PoC plugins such as Linux ELF, Android OAT, MIPS, Microsoft OLE, XLS, PPT, etc. can and will be found on our GitHub repository here: https://github.com/
The back-end APIs will be made available in the Fall 2015.
Note: This message was originally published on our Google Groups forum.
As a follow up to our last blog on Adobe PDF and Microsoft XLS plugins for JEB2, here is another example of deep analysis support in the case of nested artifacts, as is the case for Android pre-compiled native apps.
Those apps are run using ART, the newest Android Runtime. They are native Linux ELF .so files, embedding a custom Android OAT file, which in turns contains one or more Dalvik DEX bytecode files. See the pictures below for an example:
The ELF and OAT plugins will be open sourced.
Stay tuned for more news within the next few days!
As explained in our June 18 blog, JEB2 architecture and back-end API allows the development of third-party code: Plugins such as disassemblers, decompilers, parsers, or else, can be easily integrated to provide analysis capability for virtually any type of data.
We have been working on proof-of-concepts plugins for various file formats internally, such as:
An Adobe PDF file format plugin. The plugin provides deep PDF view and navigation, anomaly detection, binary correspondence, and more. Coupled with other JEB2 analysis plugins (such as a JavaScript beautifier plugin), that makes for a powerful PDF reverse-engineering tool:
A Microsoft Compound File / OLE file, for various document types, such as Excel in the pictures below:
We also have plugins for ELF object files, MIPS machine code, Android OAT resource extraction, ETC1 image reconstruction, etc.
Plugins can work on several types of input, including the output of other plugins, for recursive and deep analysis in artifact data. We are planning to open up the back-end API shortly after the full versions release, which will happen in mid July.
Some of those plugins will be open-source, we hope they provide great tutorials and insights into plugins writing for the JEB2 back-end API.
As we announced yesterday, the demo version of JEB2 beta is now available for download! We are very excited about this new product, and here is why:
This enables the creation of various front-ends: high-end customers can craft their own clients. They may be graphical, command-line based, or integrated within an automation pipeline.
Connected to that design point is the new, rich UI desktop platform, which had been on our road-map for quite some time. Our customers will now enjoy the power of Eclipse RCP as their primary official front-end.
This allows JEB2 to go beyond Android-only files. Although our primary focus stays on mobile, JEB2 is now able to support any type of binary parser, text beautifier, code disassembler, decompiler, or more generally, input transformer.
JEB2 ships with various modules designed to enable Android static analysis. Other modules will be shipped in the medium-term. Our customers will receive those modules via the traditional update channels. Some will be open-source. and available on our GitHub repository.
Application Programming Interfaces (APIs) will allow developers to write their own back-end plugins, back-end transformers, and, in the case of the official RCP front-end, client scripts. Our Full versions will ship with plugins to demonstrate what can be done with the back-end API: we will provide proof-of-concept plugins to support files such as Android OAT, Android JOBB expansion pack, Linux ELF, or MIPS binary code, to name a few.
From an immediate features perspective, JEB2 offers advanced capabilities such as virtual hierarchies and package renaming, optimized memory and computing usage when dealing with big files, multiple views and complete code hierarchies, side-by-side disassembly and decompiled code, the ability to analyze multiple artifacts within a single session.
JEB2 also supports artifact re-parsing. Recursive processing and artifact analysis delegation, manual or automatic, was a crucial design goal. We will demonstrate those capabilities in future blogs, the user manual, as well as YouTube videos.
A technical note regarding JEB 1.x to JEB2 migration:
JEB2 is moving away from the traditional “perpetual license” model. JEB2 remains a desktop software, but is now subscription-based. This allows us to:
Here are some additional details. We are currently planning to offer three plans: Standard, Business and Enterprise. The Standard package – just like the public demo build – does require an Internet connection to operate. Professional packages (Business and Enterprise) do not: they are fully-functional in air-gaps, a common industry practice when analyzing malicious code. The professional packages also offer APIs and support levels. Please refer to the pricing page for details.
Customers with a valid JEB 1.x license will receive an equivalent JEB2 subscription till the end of their current support period.
All JEB 1.x quotes that were issued before June 17, 2015, will be honored. JEB 1.x will receive fixes for major issues. We may also consult on special requests for JEB 1.x.
Finally, users with a valid JEB 1.x license will be able to use it according to the terms of the original user agreement.
The official release of JEB2 is being finalized as we speak. Most of the final tweaks will based on further internal testing and your feedback during this demo period. Give a try to the demo version of our latest beta build and let us know your comments via email, forum, or Twitter. We will continue to post on this blog to address questions and provide additional details over the coming weeks. Thank you.
We are excited to announce the coming release of JEB2, our interactive decompiler! Our terms of service as well as pricing details have changed. We encourage you to review them on our website.
In the meantime, please take a minute to download the demo version of JEB2 beta at https://www.pnfsoftware.com.
Blue Coat Systems recently released a paper about the Inception APT (also dubbed Cloud Atlas, it may be connected to the Red October APT). One component of this APT is an Android trojan, masquerading as a Whatsapp update package. It is able to record audio calls, as well as gather, encrypt and exfiltrate user information.
The 4 strings partially written in Hindi that have been speculated on are those:
For researchers wanting to have a peak inside the APK, we are providing JEB decompiled Java code for one such sample.
Download is here: cloudatlas-android-malware-decompiled.zip
The fully decompiled code and assets of 421and.apk can be found here: FinSpyMobileAndroid-decompiled.zip (no password).
This particular APK, although not the latest, is not obfuscated and easily reveals most capabilities of the malware:
A great recap of the full story can be read on Netzpolitik. Real time updates are on Twitter.