One of the new exciting features coming with JEB 4.0 is a set of signatures to identify common native libraries in a compiler-agnostic fashion.
These “codeless” signatures were built to tackle an old reverse-engineering problem: the identification of common open-source libraries in executables. Because such libraries are compiled by the developers themselves, traditional code-based signatures — like our own SigLib — need to be re-generated with the same compiler setup than the developers, otherwise the signatures won’t match because the code differs.
Therefore, identifying open-source libraries with code-based signatures is a lots of effort for a small return, because each set of signatures only matches one compiler setup (compiler’s version, optimization level…), and there is a vast number of them!
We developed codeless signatures to identify open-source libraries without the burden of signatures re-generation for each compiler setup. We are currently shipping signatures for the following libraries:
- OpenSSL, versions 0.9.8m to 1.1.1g
- libcurl, versions 7.30.0 to 7.71.1
- libssh2, versions 1.8.0, 1.8.2 and 1.9.0
- bzip2, versions 1.0.6 and 1.0.8
- zlib, versions 1.2.3, 1.2.8, 1.2.10 and 1.2.11
The signatures can be applied on any binary opened in JEB, through “Native > Codeless Signatures Libraries” menu.
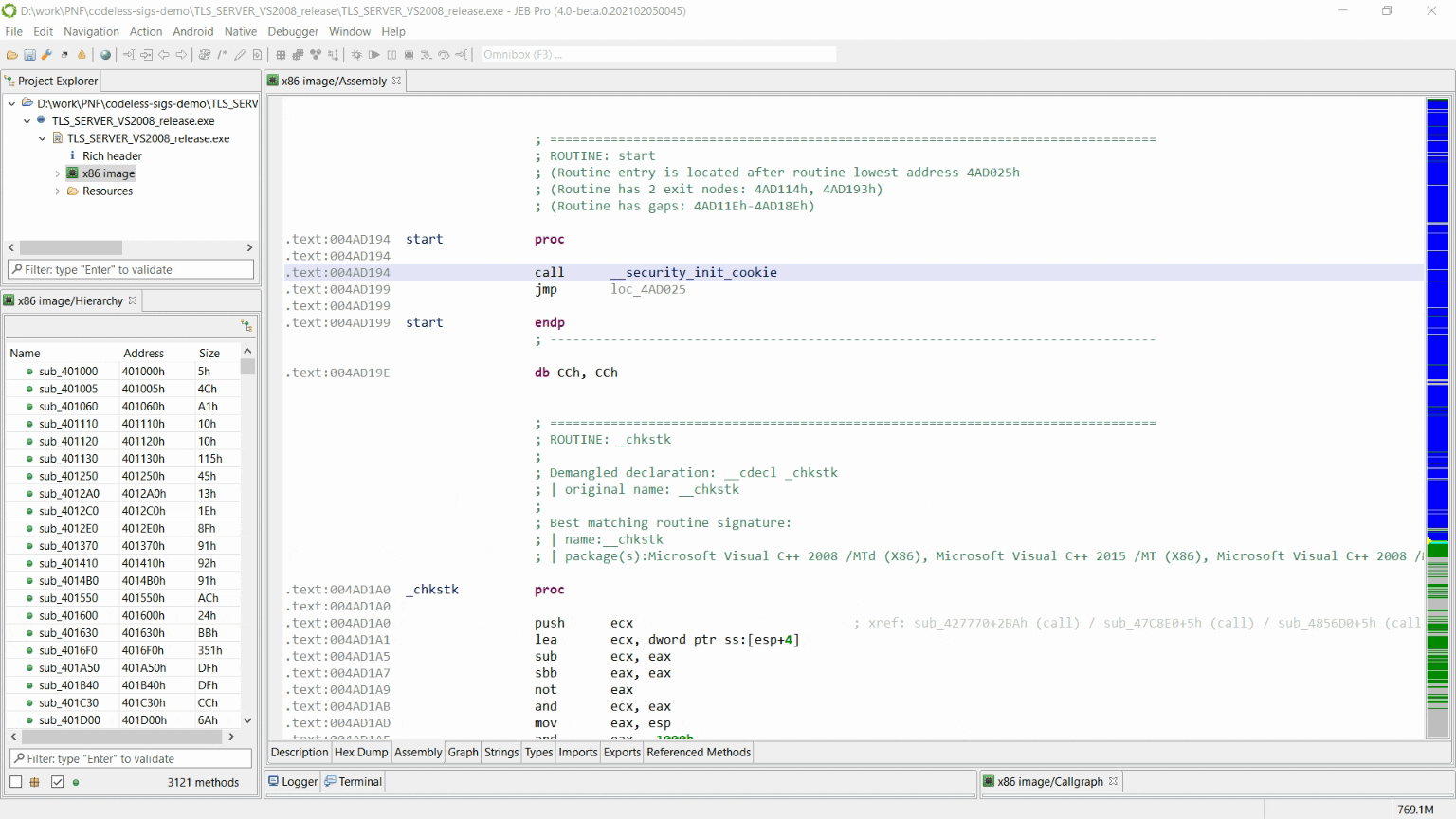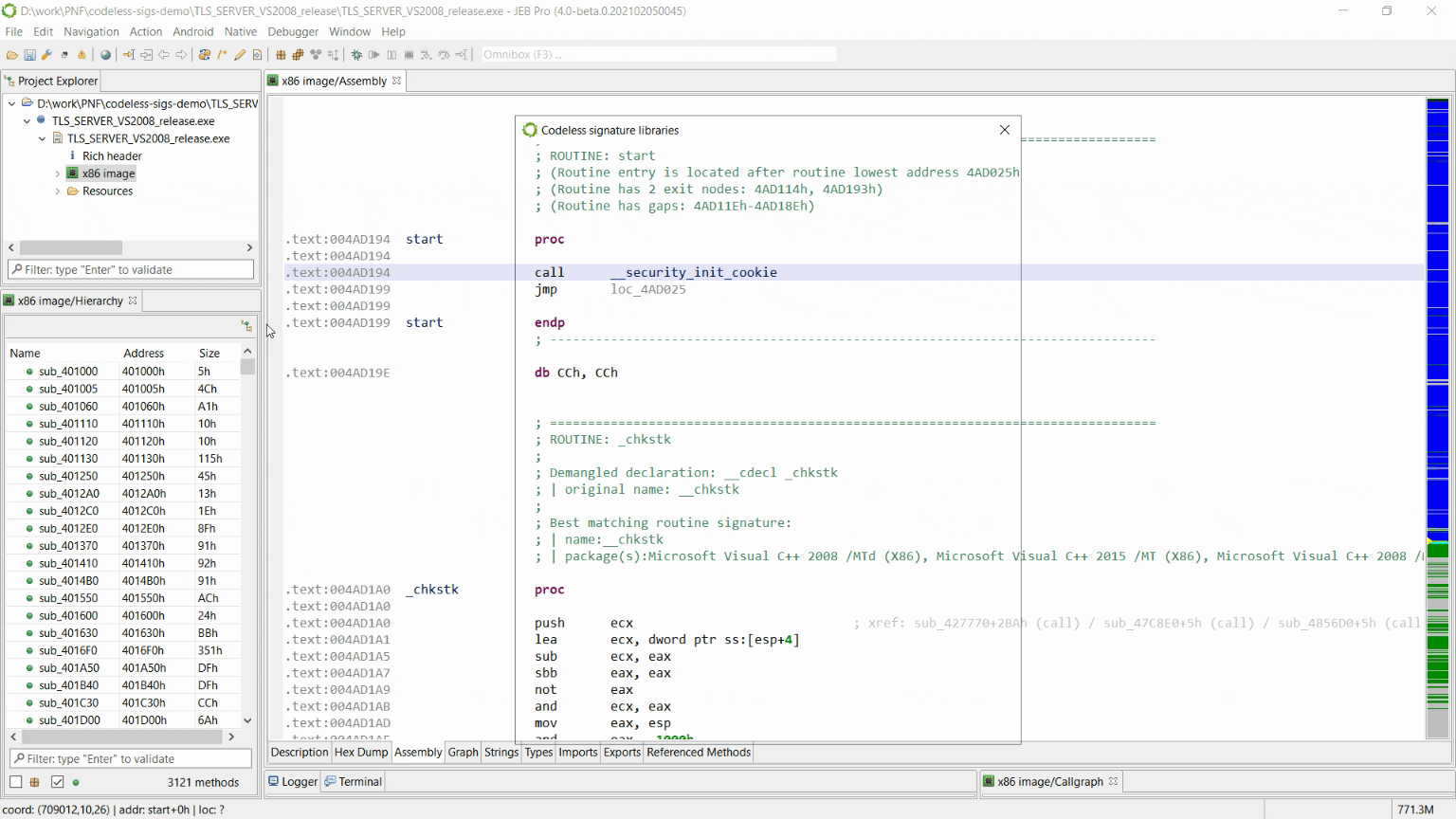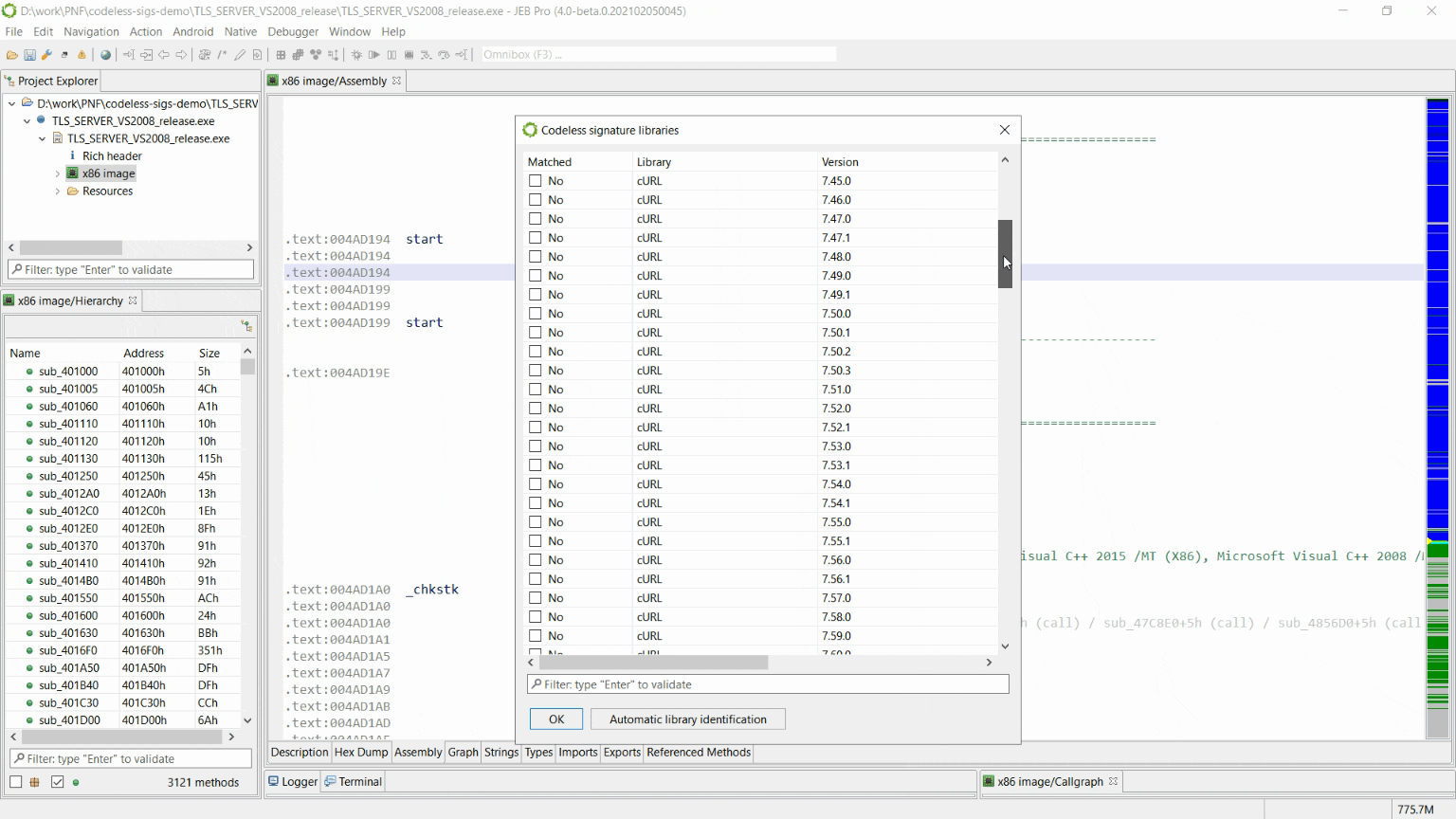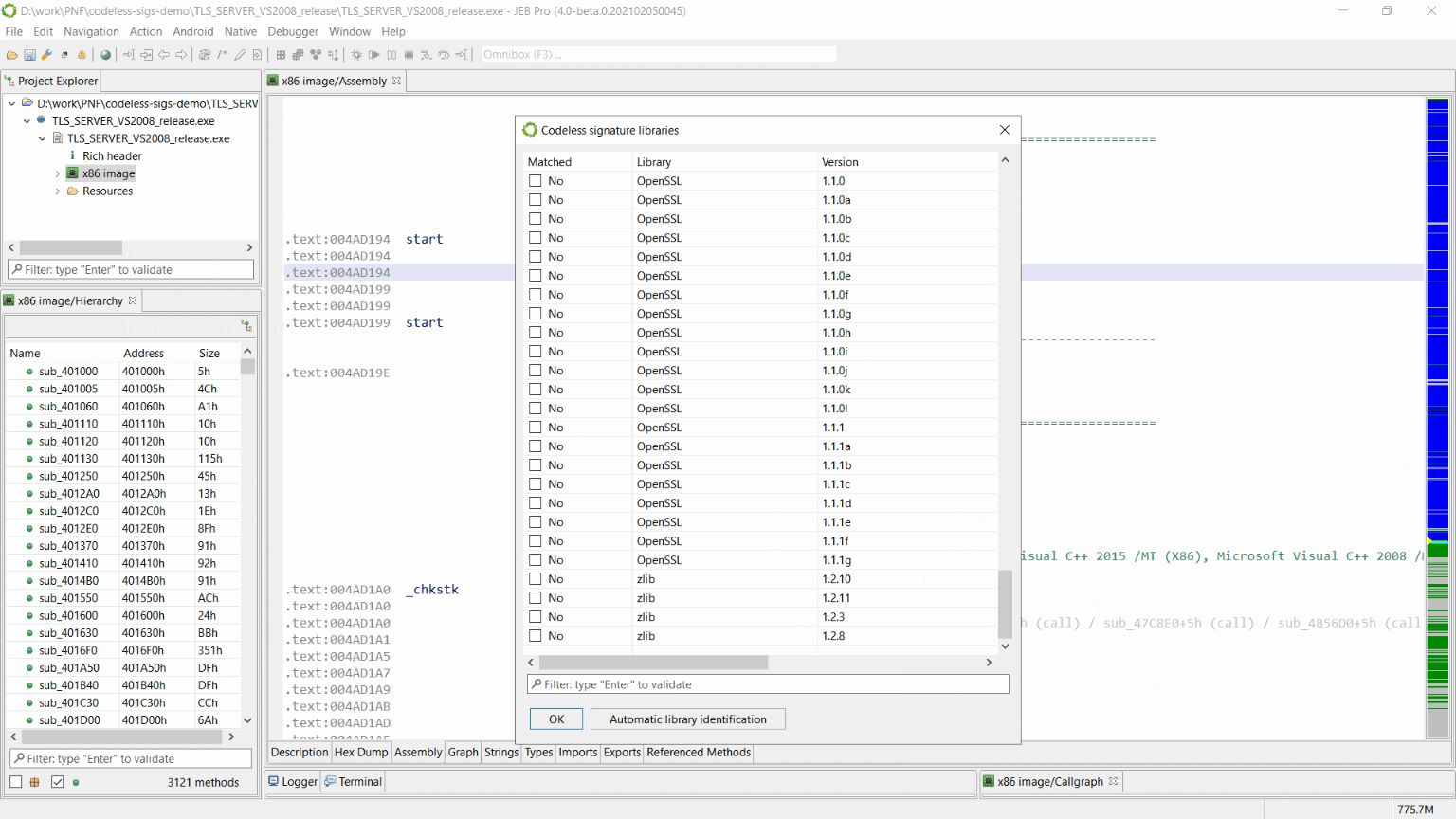
We also ship an automatic library version identification tool (available from “Codeless Signature Libraries” dialog), which should help to decide which versions of the library was linked, when it not obvious.
In order to build such signatures we made some tradeoffs, notably by accepting to miss some routines and to have a few false positives. We believe JEB’s codeless signatures are particularly suitable when one is not interested into library’s internals, and therefore the only library routines whose name really matter are the ones used by the rest of the code (like when doing malware analysis).
Overall, our current experiments show promising results, for example we usually identify 50-60% of OpenSSL routines, with a false positives ratio of less than 2%, on a variety of architecture/compiler setups.
We will describe in details the internals of JEB’s codeless signatures in an upcoming whitepaper, but in the meantime we made a video to demonstrate how to use them:
We really encourage you to test JEB’s codeless signatures and report feedback through the usual channels:
- leave a comment on this post
- email support@pnfsoftware.com
- message us on Slack
- or send us a Tweet @jebdec
Sound very interesting! Will it be also available for android?
In addition, could you release the whitepaper?
Not available for android/dalvik at the moment. The whitepaper will be released in May.